I agree to my personal data being stored and used to receive the newsletter. However, based on statistics culled from VirusTotal, we have seen malware submissions from the following countries: Attackers were able to steal hundreds of thousands of dollars from ATMS, all without attracting any attention. Detailed information on the processing of personal data can be found in the privacy policy. Replace all locks and master keys on the upper hood of the ATM machines and do not consider using the defaults provided by the manufacturer. 
| Uploader: | Maubar |
| Date Added: | 21 August 2016 |
| File Size: | 15.45 Mb |
| Operating Systems: | Windows NT/2000/XP/2003/2003/7/8/10 MacOS 10/X |
| Downloads: | 55517 |
| Price: | Free* [*Free Regsitration Required] |
Earlier this year, at the request of a financial institution, our colleagues from the Global Research and Analysis Team GReAT performed a forensic investigation into a cyber-criminal tyyupkin that targeted multiple ATMs in Eastern Europe. I have a different hash for one found in Malaysia.

In its last variant version. Based on statistics culled from VirusTotal, malware submissions have been seen from the following countries:. Secure OS file systems from any external manipulation and harden tyupkkn operating system using best security practices.
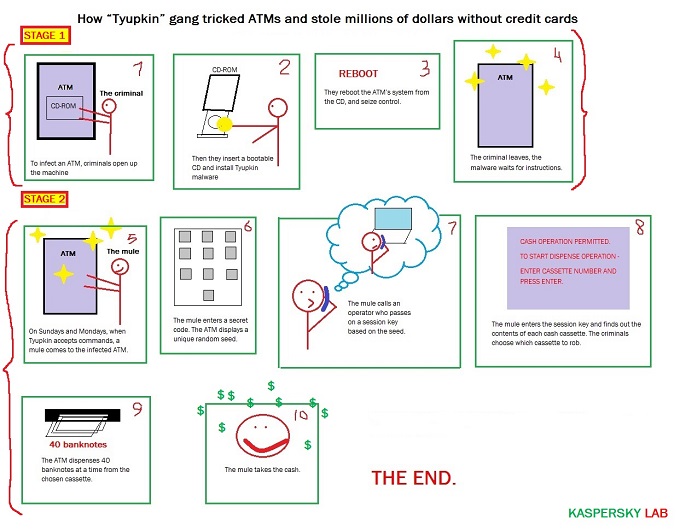
Newsletter Subscribe to our Threatpost Today newsletter Join thousands of people who receive the latest breaking cybersecurity news every day. Sponsored Content is paid for by an advertiser. Only when this key is successfully entered that it is possible to interact with the infected ATM.
One I worked on was housed in a large room that had a window going into it. The infected ATM then runs in an infinite loop waiting for a command. However this tyipkin has evolved over time. Your email address will not be published. Newsletter Subscribe to our Threatpost Today newsletter Join thousands of people who receive the latest breaking cybersecurity news every day. The fact that many ATMs run on operating systems with known security weaknesses and the absence of security solutions is another problem that thupkin to be addressed urgently.
Tyupkin Malware Infects ATMs Worldwide
Save my name, email, and website in this browser for the next time I comment. Once the malicious software was brought to life, the mules were able to draw up to 40 notes, depending on how much cash was in the machine. A unique digit combination key based on random numbers is freshly generated for every session. Why not insert a BicMac into the CD rom drive filling it with beef and special sauce so that the criminal gang can not insert their cd?
tyupjin
In a demonstration, Jack was able to bypass an authentication mechanism to trigger machines to dispense all their cash. The ATMs my bank uses are accessed from the back for that sort of thing. This ensures that no person outside the gang could accidentally profit from the fraud. The Threatpost editorial team does not participate in the writing or editing of Sponsored Content.
The successful use tyuupkin skimmers to secretly swipe credit and debit card data when customers slip their cards into ATMs at banks or gas stations is well tyupkln and has led to a greater awareness for the public to be on the lookout — and take precautions — when using public ATMs.
The gang has continued to improve Tyupkin since Kaspersky started tracking it in January, after an unnamed financial institution asked for help. How can this be possible?
Cash machine hackers have made 'millions' with Tyupkin malware | Technology | The Guardian
Third, it had the ability to disable the local network in the case of an emergency, so that the bank could not remotely connect to the ATM to check on what was happening with it. The malware waits for user input, which it accepts only on Sunday and Monday nights, the researchers said. It would have required significant planning, as the mules had to be at the infected cash machines at specified times on either Sunday or Monday nights.
In reality, all they need is an ATM with some cash in it and a special piece of software.
Each contribution has a goal of bringing a unique voice to important cybersecurity topics. In addition, learn vocabulary. Hackers gained access to dozens of ATMs and dispensed a lot of cash Tweet As the investigation showed, criminals were somehow able to physically access the ATMs so that they could install the malware via a bootable CD on an imbedded Windows machine.
In addition, you will find them in the message confirming the subscription to the newsletter. If only they did the same for their ATM assets they would not have been hit, and yes I work for one of the banks hit in KL.
For advice on how to verify that your ATMs are not currently infected, please contact Kaspersky at intelreports kaspersky. October 7, 8:

Комментариев нет:
Отправить комментарий